AISGuardian
Power. Gas. Data. Europe's critical infrastructure
runs under the Baltic Sea.
Now someone's watching.
After Nord Stream, C-Lion1, and Balticconnector, the question isn't if the next attack will happen. It's whether we'll see it coming. AISGuardian processes 5,000 vessel signals per second to detect threats before they reach critical infrastructure.
Open source. Real-time. Built on Apache Flink®.
See threats before
they reach the cable
AISGuardian ingests live vessel position data from across the Baltic Sea and runs 12 detection algorithms in parallel. When a vessel's behavior matches a threat pattern (anchor dragging toward a cable, AIS going dark, or a sanctioned ship entering monitored waters) the system alerts before damage occurs.
The key is prediction, not reaction. By analyzing trajectory and historical patterns, we can warn operators 15-45 minutes before a vessel enters a protected zone. That's the difference between prevention and post-mortem.
The Automatic Identification System (AIS) is a maritime tracking system required by the IMO on all vessels over 300 gross tonnage on international voyages, all cargo ships over 500 GT, and all passenger ships. Vessels broadcast their position, speed, course, and identity every few seconds via VHF radio.
5,000 AIS messages per second flow through Apache Flink®, with vessel state maintained in Aiven for Valkey™ for sub-second lookups.
Cross-references EU, OFAC, and Ukrainian GUR databases to track 130+ shadow fleet vessels attempting sanctions evasion.
Detects AIS spoofing, dark events, suspicious rendezvous, and convoy patterns that indicate coordinated activity.
Why I built
AISGuardian
This is a hobby project born from frustration: not a solution to national security, but a small attempt to make sense of what's moving in our waters.
The Baltic Sea carries 95% of Finland's internet traffic, all of its electricity imports from Estonia, and until recently, its gas supply. When these cables and pipelines are severed, it's not an abstract geopolitical event. It's my neighbors losing connectivity, energy prices spiking, and a country's resilience being tested.
A Strange Combination of Experience
Almost a decade in the maritime and energy industries. Years working with open-source data infrastructure. Now working with real-time data processing at Ververica, where Apache Flink was invented. Last Christmas, I watched as the Eagle S tanker severed our undersea cables. This year, I couldn't shake the thought: will we get another dragging anchor under the tree?
Everything Clicked
I know what suspicious vessel behavior looks like. I know how to build streaming pipelines that handle high-volume data. I know how powerful Flink is for stateful event processing. So I built AISGuardian: not a solution to national security, but a small attempt to make sense of what's moving in our waters.
The Gap
Existing maritime monitoring is reactive. Authorities learn about cable damage after it happens. AISGuardian detects vessels anchoring over cable routes, loitering near offshore wind farms, AIS transmission gaps in sensitive zones, and unusual speed or course changes near infrastructure.
The FITBURG Incident
On December 31st, 2025, the cook-island-flagged vessel FITBURG dragged its anchor across the Elisa submarine cable connecting Finland and Estonia, severing a critical communications link. The screenshot below shows the vessel's track as captured by AISGuardian.
This was not an isolated incident. FITBURG is part of Russia's shadow fleet: vessels operating under flags of convenience, often with obscured ownership, used to evade sanctions and, increasingly, to conduct hybrid warfare operations against European infrastructure.
AISGuardian detected FITBURG's suspicious behavior pattern before the damage occurred. The system flagged the vessel for its proximity to the cable route and unusual anchoring behavior in deep water.
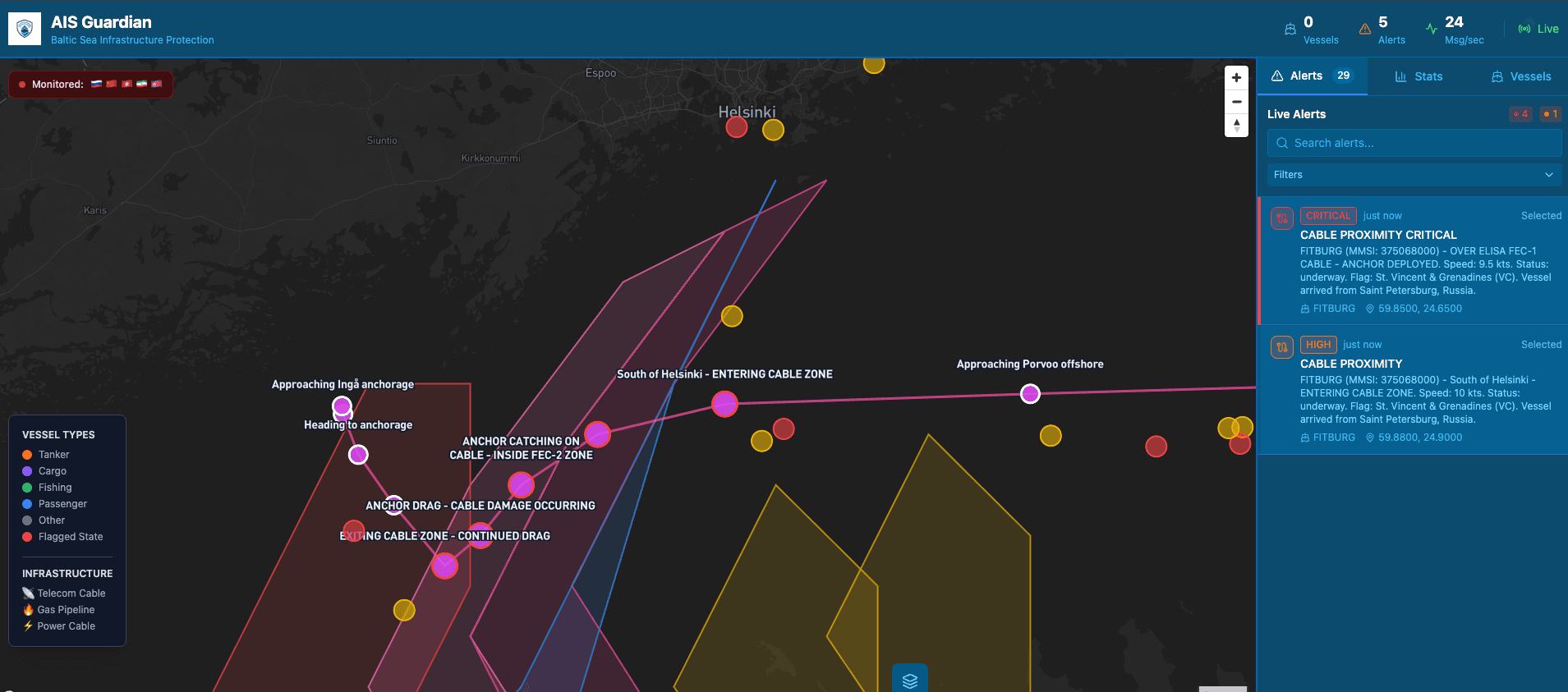
FITBURG vessel track captured by AISGuardian on December 31, 2025
The attacks have already begun
How data flows through
the system
AISGuardian processes 5,000 messages per second through a pipeline designed for real-time threat detection. Every component was chosen for its ability to handle maritime-scale data with sub-second latency.
Data Ingestion
AIS messages from AISStream.io arrive via websocket, filtered for the Baltic Sea region. Each message contains vessel position, speed, heading, and navigation status.
Message Streaming
Raw AIS data is published to Aiven for Apache Kafka® with guaranteed delivery. The topic uses 6 partitions for parallel processing, keyed by vessel MMSI.
State Enrichment
Flink jobs query Aiven for Valkey™ to enrich each message with vessel history, sanctions status, and previous alerts. Sub-millisecond lookups enable real-time processing.
Stream Processing
12 detection algorithms run in parallel across Apache Flink®. Each algorithm processes the enriched stream, evaluating threat conditions and updating vessel state.
Alert Generation
When a threat is detected, alerts are published to a dedicated Kafka topic. Critical alerts trigger immediate notifications; others are batched for analysis.
Visualization
React frontend consumes alerts and vessel positions via Server-Sent Events. Deck.gl renders 2,500+ vessels on a WebGL-accelerated map with real-time updates.
Open source infrastructure
for real-time systems
Open source is one of humanity's greatest gifts: thousands of engineers contributing to shared infrastructure that anyone can use. AISGuardian runs on Apache Kafka®, Apache Flink®, and Valkey™, the same battle-tested technologies that power the world's most demanding systems. But open source alone isn't enough. It's managed platforms like Aiven's and Ververica's that turn this gift into something a single person can actually use, with no infrastructure overhead and at minimal cost. I built this entire system on my own. That would have been impossible five years ago.
Aiven for Apache Kafka®
Kafka is the backbone of AISGuardian. Every AIS message, alert, and state update flows through it. With 5,000 messages per second, I needed a platform that could handle the throughput without operational overhead.
Why managed Kafka?
- Production-ready in minutes, not weeks of configuration
- Built-in schema registry for AIS message validation
- Automatic topic compaction keeps vessel state history manageable
- Cross-region replication ready for disaster recovery
Aiven Console: Kafka in Action
Aiven for Valkey™
Valkey handles two critical functions: trail persistence (storing 72 hours of vessel movement history for visualization and pattern analysis) and state storage (maintaining detector state across Flink restarts, caching sanctions lists, and storing alert history).
Why managed Valkey?
- Sub-millisecond reads enable real-time enrichment without buffering
- Automatic persistence ensures state survives restarts
- Pub/Sub channels push alerts to the frontend instantly
- Memory-efficient data structures for geospatial queries
Aiven Console: Valkey Metrics
Apache Flink® on Ververica Cloud
Flink is where the detection magic happens. 12 algorithms run in parallel, each consuming the enriched AIS stream and evaluating threat conditions in real-time. Ververica Cloud, built by the creators of Flink, provides the managed infrastructure that makes this possible.
Why Ververica?
- Built by the team that created Apache Flink
- Managed deployment with automatic scaling and failover
- Native Kafka integration for seamless data flow
- Real-time metrics and job monitoring dashboard
Ververica Cloud: Flink Jobs in Action
Real-time view of AISGuardian's Flink jobs processing vessel data on Ververica Cloud
12 detection algorithms
running in parallel
Infrastructure Protection
- Cable proximity monitoring with 15-45 minute advance warning
- Anchor dragging detection before damage occurs
- Trajectory prediction using historical patterns
- Geofence violations for restricted zones
Sanctions Enforcement
- Shadow fleet tracking from EU, OFAC, and Ukraine GUR databases
- Persistent vessel tracking that never loses sight of bad actors
- Risk scoring based on port visits, dark events, and behavior
- High-risk flag monitoring (Russia, Iran, North Korea)
Behavioral Analysis
- Dark AIS detection: vessels going silent or appearing unexpectedly
- AIS spoofing detection: identity theft, impossible positions
- Rendezvous detection: ship-to-ship meetings in open water
- Pattern analysis: convoys, fishing in protected areas
Built to be
replicated and improved
AISGuardian is fully open source under the MIT license. The architecture, detection algorithms, and deployment configurations are all available on GitHub. If you're building maritime surveillance, sanctions enforcement, or infrastructure protection systems, this codebase is designed to be your starting point.
The Baltic Sea problem is global
What's happening in the Baltic (systematic attacks on critical infrastructure) will happen elsewhere. The South China Sea, the Mediterranean, the English Channel. AISGuardian's architecture can be deployed anywhere AIS data is available. The detection algorithms are agnostic to geography. The Aiven + Flink stack scales to any maritime region.
This project exists because I believe real-time threat detection should be accessible to any organization protecting critical infrastructure. The code is free. The knowledge is shared. The only cost is the compute.
Career Paths Make Sense in Retrospect
I worked for three years watching customers build real-time systems and helping them realize the value of their real-time data. Building AISGuardian was a chance to apply that knowledge to a problem I care about. The platforms I used to recommend to others are now the foundation of my own project.
Let's build something
worth talking about.
I take on a limited number of advisory and fractional engagements. Only projects where I can make a real difference. If you're navigating growth, AI, or revenue challenges in a technical B2B environment, let's talk.